
- Advanced malware discovery
- Used by forensic labs, law enforcement, field investigators, private investigators, and incident response teams
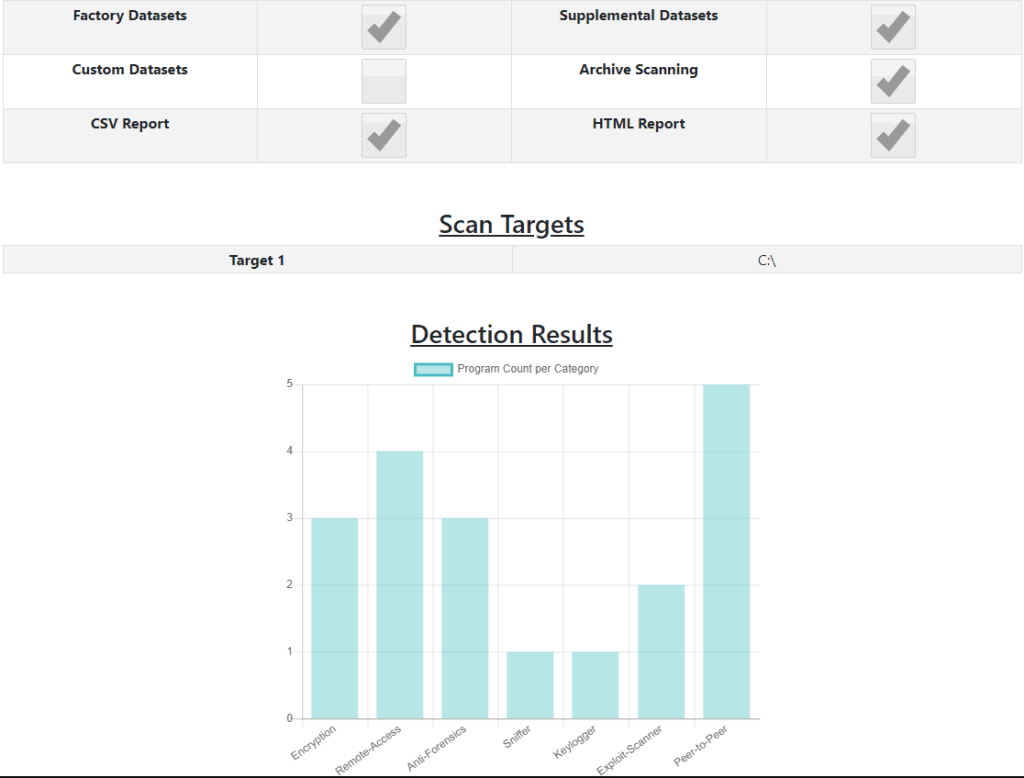
- Rapid search of malicious applications
- Comprehensive reporting
Gargoyle Investigator™ MP is the next generation of WetStone’s advanced malware discovery solution for computer forensic investigators and incident response teams. It is designed for forensic laboratories, law enforcement, field investigators, advanced private investigators, and enterprise cyber security personnel. Gargoyle performs a rapid search for malicious applications and provides significant clues regarding the activities, motives and intent of a suspect.
Gargoyle Investigator™ MP takes everything that its current users know and love about Gargoyle Investigator and improves upon it. Its new, modern codebase, faster scan times, and improved archive and file format processing make Gargoyle Investigator™ MP a great improvement over the previous generation of Gargoyle Investigator™.

Gargoyle MP is designed to simplify your breach and malware triage investigation and incident response activities. Gargoyle MP enables users to perform a rapid search for known contraband, hostile programs and lost or leaked corporate assets.
FEATURES OF GARGOYLE INVESTIGATOR™ MP
- Advanced malware discovery
- Used by forensic labs, law enforcement, field investigators, private investigators, and incident response teams
- Rapid search of malicious applications
- Comprehensive reporting
- Compatible with a variety of Windows desktop platforms:
- Windows 7
- Windows 8
- Windows 8.1
- Windows 10
- Compatible with a variety of Windows Server platforms:
- Windows Server 2008 and 2008 R2
- Windows Server 2012 and 2012 R2
- Windows Server 2016
WHAT TYPES OF PROGRAMS CAN GARGOYLE MP DETECT?
WetStone Technologies searches for and maintains a malware repository for each of the following program categories:
- Anti-forensics
- Botnet
- Cryptojacking
- Cryptomining
- Denial of service
- Encryption
- Exploit Kit
- Exploit scanner
- Fraud tools
- Keylogger
- OSINT
- Password cracking
- Peer-to-peer
- Piracy
- Ransomware
- Remote access
- Rootkit
- Scareware
- Sniffer
- Spyware
- Toolkit
- Trojan
- Web threats
- Wireless tools
INTEGRATIONS
Gargoyle has the ability to scan comma separated value files, commonly referred to as CSV files of MD5 Hashes. The format of the file is both simple and strict. This allows Gargoyle to scan hash results for malicious code or cyber weapons from virtually any forensic collection platform.
Gargoyle currently integrates with the following platforms:
Encase® Forensic by Guidance Software
WetStone includes an EnScript with Gargoyle Investigator MP. The EnScript will export a hash file from EnCase that will be formatted as comma-delimited file that has the hash file field definitions Gargoyle can scan.
Forensic Explorer by GetData
WetStone allows for an export file from Forensic Explorer to be selected in the hash file section of the user interface of Gargoyle. Gargoyle will then automatically format the data into the hash file field definitions Gargoyle recognizes before it scans the file.
DELIVERABLE
- Your choice of either Electronic Software Download (ESD) or FLASH license type (USB device) for Gargoyle MP
- Access to monthly Dataset updates
- Customer support portal account
- 1-year software maintenance
LICENSING TYPES
- ESD: Electronic software download for use on a single system.Available as a perpetual or subscription license. Not transferable. Basic license is 2 cores, additional core licensing available.
- FLASH: 16GB USB 3.0 device for use in field investigations, and on multiple systems. Limited to 2 cores.
Schedule a Demonstration
